Sabtu, 18 Februari 2012
Tugas KKPI
1.Database adalah kumpulan informasi yang disimpan di dalam komputer secara sistematik sehingga dapat diperiksa menggunakan suatu program komputer untuk memperoleh informasi dari basis data tersebut.
2.Database Relational adalah sebuah database yang terdiri dari koleksi dari tabel-tabel, yang masing-masing diberikan nama yang unik. Sebuah baris dalam tabel merepresentasikan sebuah keterhubungan/relationship dari beberapa nilai yang ada.
3.DBMS (DataBase Management System) adalah sistem yang secara khusus dibuat untuk memudahkan pemakai dalam mengelola basis data. Sistem ini dibuat untuk mengatasi kelemahan sistem pemrosesan yang berbasis berkas.
4.Program aplikasi adalah software program yang memiliki aktivitas pemrosesan perintah yang diperlukan untuk melaksanakan permintaan pengguna dengan tujuan tertentu
5.Sistem data base merupakan perpaduan antarabasis data dan system manajemen basis data (SMBD).
6.Data adalah himpunan simbol atau fakta mentah yang tidak mempunyai arti dan nilai apapun secara tersendiri.
7.Informasi adalah data yang telah diproses menjadi bentuk yang memiliki arti bagi penerima dan dapat berupa fakta, suatu nilai yang bermanfaat.
8.Tabel adalah kumpulan dari beberapa record dan fields. jadi yang dimaksud dengan fields adalah atribut yang dimiliki oleh suatu tabel.
9.Formulir adalah secarik kertas yang memiliki ruang untuk diisi dengan data penting tertentu.
10.Record adalah kumpulan elemen-elemen data yang digabungkan menjadi satu kesatuan, masing-nasing elemen data tersebut dikenal dengan sebutan field.
11.Query adalah merupakan bahasa untuk melakukan manipulasi terhadap database, yang telah distandarkan dan lebih dikenal dengan nama Structured Query Language (SQL).
12.Field adalah sebuah unit data yang berisi satu atau lebih karakter (byte).
13.Report adalah file yang berisi data yang dibuat untuk laporan atau keperluan user. File tersebut dapat dicetak pada kertas printer atau hanya ditampilkan dilayar.
14.Primary Key adalah atribut (field) yang dipilih untuk menentukan struktur storage pada organisasi file multi key, adapun key lainnya disebut dengan secondary key.
2.Database Relational adalah sebuah database yang terdiri dari koleksi dari tabel-tabel, yang masing-masing diberikan nama yang unik. Sebuah baris dalam tabel merepresentasikan sebuah keterhubungan/relationship dari beberapa nilai yang ada.
3.DBMS (DataBase Management System) adalah sistem yang secara khusus dibuat untuk memudahkan pemakai dalam mengelola basis data. Sistem ini dibuat untuk mengatasi kelemahan sistem pemrosesan yang berbasis berkas.
4.Program aplikasi adalah software program yang memiliki aktivitas pemrosesan perintah yang diperlukan untuk melaksanakan permintaan pengguna dengan tujuan tertentu
5.Sistem data base merupakan perpaduan antarabasis data dan system manajemen basis data (SMBD).
6.Data adalah himpunan simbol atau fakta mentah yang tidak mempunyai arti dan nilai apapun secara tersendiri.
7.Informasi adalah data yang telah diproses menjadi bentuk yang memiliki arti bagi penerima dan dapat berupa fakta, suatu nilai yang bermanfaat.
8.Tabel adalah kumpulan dari beberapa record dan fields. jadi yang dimaksud dengan fields adalah atribut yang dimiliki oleh suatu tabel.
9.Formulir adalah secarik kertas yang memiliki ruang untuk diisi dengan data penting tertentu.
10.Record adalah kumpulan elemen-elemen data yang digabungkan menjadi satu kesatuan, masing-nasing elemen data tersebut dikenal dengan sebutan field.
11.Query adalah merupakan bahasa untuk melakukan manipulasi terhadap database, yang telah distandarkan dan lebih dikenal dengan nama Structured Query Language (SQL).
12.Field adalah sebuah unit data yang berisi satu atau lebih karakter (byte).
13.Report adalah file yang berisi data yang dibuat untuk laporan atau keperluan user. File tersebut dapat dicetak pada kertas printer atau hanya ditampilkan dilayar.
14.Primary Key adalah atribut (field) yang dipilih untuk menentukan struktur storage pada organisasi file multi key, adapun key lainnya disebut dengan secondary key.
Jumat, 17 Februari 2012
Kabel Cross dan Straight
0
komentar
Diposting oleh
Yully Christiawaty at 18.28
Label: http://id.istanto.net/2010/02/26/kabel-straight-dan-kabel-cross/
Label: http://id.istanto.net/2010/02/26/kabel-straight-dan-kabel-cross/
Banyak lulusan TI Indonesia yang kemarin
di rendahkan (dilecehkan) ketika melamar pekerjaan hanya karena tidak
menguasai dasar-dasar jenis per-kabelan. Berita tentang TI Indonesia yang mengecewakan ini sampai sempat membuat beberapa orang panas. Panasnya kenapa? ada yang memang tidak tau menau tapi hanya ikutan “asal ngomong”
ada yang begini-begitu tapi ternyata ada saja alasannya, kenapa kita
harus teriak omong kosong kalau tidak mau menerima kritik dan belajar.
Memang umum-nya lulusan TI jaman
sekarang ini saya rasa belum siap untuk bekerja di bidangnya. Karena
teknologi yang selalu berkembang sehingga terkadang beberapa lulusan TI
ini merasa “mampu” padahal sebenarnya pemahaman dasar-nya dia tidak
punya. Kurikulum yang di kembangkan kampus juga terkadang tidak relevan
dengan realita yang ada di lapangan. Sehingga rasanya terkesan lebih
pandai orang yang terbiasa menggunakan dan ber-eksperimen di bandingkan
dengan orang yang hanya membahas teori.
Dalam artikel ini akan saya berikan
sedikit penjelasan tentang jenis-jenis per-kabelan, mudah-mudahan bisa
membuka wawasan dan membantu beberapa orang yang memang benar-benar
BUTA.
Peralatan dan media yang di butuhkan:

Urutan Ujung A
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Menghubungkan PC dengan HUB/Switch.

Urutan Ujung A
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Putih Hijau
- Hijau
- Putih Orange
- Putih Coklat
- Coklat
- Orange
- Biru
- Putih Biru
- Menghubungkan PC ke PC langsung tanpa HUB/Switch.
- Menghubungkan HUB/Swicth dengan HUB/Switch.
Kita akan coba membuat kabel straight,
pertama kupas-lah pelindung luar kabel UTP lalu atur agar lurus
kabel-kabel didalamnya. Urutkan posisinya berdasarkan diagram diatas.
Potong ujung kabel dengan gunting agar rata. Masukkan kedalam konektor
RJ-45 lalu di crimping dengan tang crimping. Ikuti caranya untuk ujung
kedua sama dengan langkah pertama. Masukkan ujung kedua kabel kedalam
LAN-tester lalu periksa, jika semua lampu 1-8 terhubung maka kabel ini
sudah siap kita pakai.
Untuk kabel cross juga sama seperti
langkah diatas, hanya bedanya harap perhatikan salah satu ujung yang
berbeda. Adapun standard per-kabelan ini yang dijaminkan adalah kurang
lebh 100 meter, diatas 100 meter kemungkinan akan mengalami loss.
Jika ada yang bertanya bagaimana
membedakan kabel straight dan kabel cross? Sebenarnya mudah saja,
perhatikan ujung dari kedua kabel tersebut lihat diagram-nya bila yang
pertama adalah putih orange lalu kedua putih orange juga sudah pasti itu
kabel straight, sedangkan kabel cross salah satu ujungnya dimulai
dengan putih hijau.
IP V4
Internet Protocol version 4 (IPv4) is the fourth revision in the development of the Internet Protocol (IP) and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet. IPv4 is still by far the most widely deployed Internet Layer protocol (As of 2011, IPv6 deployment is still in its infancy).
IPv4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition (RFC 760, January 1980).
IPv4 is a connectionless protocol for use on packet-switched Link Layer networks (e.g., Ethernet). It operates on a best effort delivery model, in that it does not guarantee delivery, nor does it assure proper sequencing or avoidance of duplicate delivery. These aspects, including data integrity, are addressed by an upper layer transport protocol , such as the Transmission Control Protocol (TCP).
This limitation stimulated the development of IPv6 in the 1990s, which has been in commercial deployment since 2006.
The following table shows several representation formats:
To overcome this limit, the high order octet of the addresses was redefined to create a set of classes of networks, in a system which later became known as classful networking. The system defined five classes, Class A, B, C, D, and E. The Classes A, B, and C had different bit lengths for the new network identification. The rest of an address was used as previously to identify a host within a network, which meant that each network class had a different capacity to address hosts. Class D was allocated for multicast addressing and Class E was reserved for future applications.
Starting around 1985, methods were devised to allow IP networks to be subdivided. The concept of the variable-length subnet mask (VLSM) was introduced which allowed flexible subdivision into varying network sizes.[2][3]
Around 1993, this system of classes was officially replaced with Classless Inter-Domain Routing (CIDR), and the class-based scheme was dubbed classful, by contrast.
CIDR was designed to permit repartitioning of any address space so that smaller or larger blocks of addresses could be allocated to users. The hierarchical structure created by CIDR is managed by the Internet Assigned Numbers Authority (IANA) and the regional Internet registries (RIRs). Each RIR maintains a publicly-searchable WHOIS database that provides information about IP address assignments.
The following are the three ranges reserved for private networks (RFC 1918):
VPNs establish tunneling connections across the public network such that the endpoints of the tunnel function as routers for packets from the private network. In this routing function the host encapsulates packets in a protocol layer with packet headers acceptable in the public network so that they may be delivered to the opposing tunnel end point where the additional protocol layer is removed and the packet is delivered locally to its intended destination.
Optionally, encapsulated packets may be encrypted to secure the data while it travels over the public network.
When the address block was reserved, no standards existed for mechanisms of address autoconfiguration. Filling the void, Microsoft created an implementation called Automatic Private IP Addressing (APIPA). Due to Microsoft's market power, APIPA has been deployed on millions of machines and has, thus, become a de facto standard in the industry. Many years later, the IETF defined a formal standard for this functionality, RFC 3927, entitled Dynamic Configuration of IPv4 Link-Local Addresses.
Classful addressing prescribed only three possible subnet masks: Class A, 255.0.0.0 or /8; Class B, 255.255.0.0 or /16; and Class C, 255.255.255.0 or /24. For example, in the subnet 192.168.5.0/255.255.255.0 (192.168.5.0/24) the identifier 192.168.5.0 commonly is used to refer to the entire subnet. To avoid ambiguity in representation, the address ending in the octet 0 is reserved.
A broadcast address is an address that allows information to be sent to all interfaces in a given subnet, rather than a specific machine. Generally, the broadcast address is found by obtaining the bit complement of the subnet mask and performing a bitwise OR operation with the network identifier. In other words, the broadcast address is the last address in the address range of the subnet. For example, the broadcast address for the network 192.168.5.0 is 192.168.5.255. For networks of size /24 or larger, the broadcast address always ends in 255.
However, this does not mean that every address ending in 0 or 255 cannot be used as a host address. For example, in the case of a /16 subnet 192.168.0.0/255.255.0.0, equivalent to the address range 192.168.0.0–192.168.255.255, the broadcast address is 192.168.255.255. However, one may assign 192.168.1.255, 192.168.2.255, etc. 192.168.0.0 is the network identifier which should not be assigned to an interface,[4] but 192.168.1.0, 192.168.2.0, etc. may be assigned.
In the past, conflict between network addresses and broadcast addresses arose because some software used non-standard broadcast addresses with zeros instead of ones.[5]
In networks smaller than /24, broadcast addresses do not necessarily end with 255. For example, a CIDR subnet 203.0.113.16/28 has the broadcast address 203.0.113.31.
The translation between addresses and domain names is performed by the Domain Name System (DNS), a hierarchical, distributed naming system which allows for subdelegation of name spaces to other DNS servers. DNS is often described in analogy to the telephone system directory information systems in which subscriber names are translated to telephone numbers.
Several market forces have driven the acceleration of IPv4 address exhaustion:
The accepted and standardized solution is the migration to Internet Protocol Version 6. The address size was increased in IPv6 to 128 bits, providing a vastly increased address space that also allows improved route aggregation across the Internet and offers large subnetwork allocations of a minimum of 264 host addresses to end-users. Migration to IPv6 is in progress but completion is expected to take considerable time.
IPv4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition (RFC 760, January 1980).
IPv4 is a connectionless protocol for use on packet-switched Link Layer networks (e.g., Ethernet). It operates on a best effort delivery model, in that it does not guarantee delivery, nor does it assure proper sequencing or avoidance of duplicate delivery. These aspects, including data integrity, are addressed by an upper layer transport protocol , such as the Transmission Control Protocol (TCP).
| Internet protocol suite |
|---|
| Application layer |
| Transport layer |
| Internet layer |
| Link layer |
Contents[hide] |
[edit] Addressing
IPv4 uses 32-bit (four-byte) addresses, which limits the address space to 4294967296 (232) addresses. However, some address blocks are reserved for special purposes such as private networks (~18 million addresses) and multicast addresses (~270 million addresses). This reduces the number of addresses that may be allocated for routing on the public Internet. As addresses are assigned to end users, an IPv4 address shortage has been developing. Network addressing changes by classful network design, Classless Inter-Domain Routing, and network address translation (NAT) have contributed to delay significantly the inevitable exhaustion which occurred on February 3, 2011 when IANA allocated the last five blocks to the five regional Internet registries (RIRs).This limitation stimulated the development of IPv6 in the 1990s, which has been in commercial deployment since 2006.
[edit] Address representations
IPv4 addresses may be written in any notation expressing a 32-bit integer value, but for human convenience, they are most often written in dot-decimal notation, which consists of four octets of the address expressed individually in decimal and separated by periods.The following table shows several representation formats:
| Notation | Value | Conversion from dot-decimal |
|---|---|---|
| Dot-decimal notation | 192.0.2.235 | N/A |
| Dotted Hexadecimal[1] | 0xC0.0x00.0x02.0xEB | Each octet is individually converted to hexadecimal form |
| Dotted Octal[1] | 0300.0000.0002.0353 | Each octet is individually converted into octal |
| Hexadecimal | 0xC00002EB | Concatenation of the octets from the dotted hexadecimal |
| Decimal | 3221226219 | The 32-bit number expressed in decimal |
| Octal | 030000001353 | The 32-bit number expressed in octal |
[edit] Allocation
Originally, an IP address was divided into two parts, the network identifier represented in the most significant (highest order) octet of the address and the host identifier using the rest of the address. The latter was therefore also called the rest field. This enabled the creation of a maximum of 256 networks. This was quickly found to be inadequate.To overcome this limit, the high order octet of the addresses was redefined to create a set of classes of networks, in a system which later became known as classful networking. The system defined five classes, Class A, B, C, D, and E. The Classes A, B, and C had different bit lengths for the new network identification. The rest of an address was used as previously to identify a host within a network, which meant that each network class had a different capacity to address hosts. Class D was allocated for multicast addressing and Class E was reserved for future applications.
Starting around 1985, methods were devised to allow IP networks to be subdivided. The concept of the variable-length subnet mask (VLSM) was introduced which allowed flexible subdivision into varying network sizes.[2][3]
Around 1993, this system of classes was officially replaced with Classless Inter-Domain Routing (CIDR), and the class-based scheme was dubbed classful, by contrast.
CIDR was designed to permit repartitioning of any address space so that smaller or larger blocks of addresses could be allocated to users. The hierarchical structure created by CIDR is managed by the Internet Assigned Numbers Authority (IANA) and the regional Internet registries (RIRs). Each RIR maintains a publicly-searchable WHOIS database that provides information about IP address assignments.
[edit] Special-use addresses
Main article: Reserved IP addresses#Reserved IPv4 addresses
| CIDR address block | Description | Reference |
|---|---|---|
| 0.0.0.0/8 | Current network (only valid as source address) | RFC 1700 |
| 10.0.0.0/8 | Private network | RFC 1918 |
| 127.0.0.0/8 | Loopback | RFC 5735 |
| 169.254.0.0/16 | Link-Local | RFC 3927 |
| 172.16.0.0/12 | Private network | RFC 1918 |
| 192.0.0.0/24 | Reserved (IANA) | RFC 5735 |
| 192.0.2.0/24 | TEST-NET-1, Documentation and example code | RFC 5735 |
| 192.88.99.0/24 | IPv6 to IPv4 relay | RFC 3068 |
| 192.168.0.0/16 | Private network | RFC 1918 |
| 198.18.0.0/15 | Network benchmark tests | RFC 2544 |
| 198.51.100.0/24 | TEST-NET-2, Documentation and examples | RFC 5737 |
| 203.0.113.0/24 | TEST-NET-3, Documentation and examples | RFC 5737 |
| 224.0.0.0/4 | Multicasts (former Class D network) | RFC 3171 |
| 240.0.0.0/4 | Reserved (former Class E network) | RFC 1700 |
| 255.255.255.255 | Broadcast | RFC 919 |
[edit] Private networks
Of the approximately four billion addresses allowed in IPv4, three ranges of address are reserved for use in private networks. These ranges are not routable outside of private networks and private machines cannot directly communicate with public networks. They can, however, do so through network address translation.The following are the three ranges reserved for private networks (RFC 1918):
| Name | Address range | Number of addresses | Classful description | Largest CIDR block |
|---|---|---|---|---|
| 24-bit block | 10.0.0.0–10.255.255.255 | 16777216 | Single Class A | 10.0.0.0/8 |
| 20-bit block | 172.16.0.0–172.31.255.255 | 1048576 | Contiguous range of 16 Class B blocks | 172.16.0.0/12 |
| 16-bit block | 192.168.0.0–192.168.255.255 | 65536 | Contiguous range of 256 Class C blocks | 192.168.0.0/16 |
[edit] Virtual private networks
Packets with a private destination address are ignored by all public routers. Therefore, it is not possible to communicate directly between two private networks (e.g., two branch offices) via the public Internet. This requires the use of IP tunnels or a virtual private network (VPN).VPNs establish tunneling connections across the public network such that the endpoints of the tunnel function as routers for packets from the private network. In this routing function the host encapsulates packets in a protocol layer with packet headers acceptable in the public network so that they may be delivered to the opposing tunnel end point where the additional protocol layer is removed and the packet is delivered locally to its intended destination.
Optionally, encapsulated packets may be encrypted to secure the data while it travels over the public network.
[edit] Link-local addressing
Main article: Link-local address
RFC 5735
defines an address block, 169.254.0.0/16, for the special use in
link-local addressing. These addresses are only valid on the link, such
as a local network segment or point-to-point connection, that a host is
connected to. These addresses are not routable and like private
addresses cannot be the source or destination of packets traversing the
Internet. Link-local addresses are primarily used for address
autoconfiguration (Zeroconf) when a host cannot obtain an IP address from a DHCP server or other internal configuration methods.When the address block was reserved, no standards existed for mechanisms of address autoconfiguration. Filling the void, Microsoft created an implementation called Automatic Private IP Addressing (APIPA). Due to Microsoft's market power, APIPA has been deployed on millions of machines and has, thus, become a de facto standard in the industry. Many years later, the IETF defined a formal standard for this functionality, RFC 3927, entitled Dynamic Configuration of IPv4 Link-Local Addresses.
[edit] Localhost
Main article: localhost
The address range 127.0.0.0–127.255.255.255 (127.0.0.0/8 in CIDR notation) is reserved for localhost
communication. Addresses within this range should never appear outside a
host computer and packets sent to this address are returned as incoming
packets on the same virtual network device (known as loopback).[edit] Addresses ending in 0 or 255
Main article: IPv4 subnetting reference
Networks with subnet masks of at least 24 bits, i.e. Class C networks
in classful networking, and networks with CIDR prefixes /24 to /32
(255.255.255.0–255.255.255.255) may not have an address ending in 0 or
255.Classful addressing prescribed only three possible subnet masks: Class A, 255.0.0.0 or /8; Class B, 255.255.0.0 or /16; and Class C, 255.255.255.0 or /24. For example, in the subnet 192.168.5.0/255.255.255.0 (192.168.5.0/24) the identifier 192.168.5.0 commonly is used to refer to the entire subnet. To avoid ambiguity in representation, the address ending in the octet 0 is reserved.
A broadcast address is an address that allows information to be sent to all interfaces in a given subnet, rather than a specific machine. Generally, the broadcast address is found by obtaining the bit complement of the subnet mask and performing a bitwise OR operation with the network identifier. In other words, the broadcast address is the last address in the address range of the subnet. For example, the broadcast address for the network 192.168.5.0 is 192.168.5.255. For networks of size /24 or larger, the broadcast address always ends in 255.
However, this does not mean that every address ending in 0 or 255 cannot be used as a host address. For example, in the case of a /16 subnet 192.168.0.0/255.255.0.0, equivalent to the address range 192.168.0.0–192.168.255.255, the broadcast address is 192.168.255.255. However, one may assign 192.168.1.255, 192.168.2.255, etc. 192.168.0.0 is the network identifier which should not be assigned to an interface,[4] but 192.168.1.0, 192.168.2.0, etc. may be assigned.
In the past, conflict between network addresses and broadcast addresses arose because some software used non-standard broadcast addresses with zeros instead of ones.[5]
In networks smaller than /24, broadcast addresses do not necessarily end with 255. For example, a CIDR subnet 203.0.113.16/28 has the broadcast address 203.0.113.31.
[edit] Address resolution
Main article: Domain Name System
Hosts on the Internet
are usually known by names, e.g., www.example.com, not primarily by
their IP address, which is used for routing and network interface
identification. The use of domain names requires translating, called resolving, them to addresses and vice versa. This is analogous to looking up a phone number in a phone book using the recipient's name.The translation between addresses and domain names is performed by the Domain Name System (DNS), a hierarchical, distributed naming system which allows for subdelegation of name spaces to other DNS servers. DNS is often described in analogy to the telephone system directory information systems in which subscriber names are translated to telephone numbers.
[edit] Address space exhaustion
Main article: IPv4 address exhaustion
Since the 1980s it was apparent that the pool of available IPv4
addresses was depleted at a rate that was not initially anticipated in
the original design of the network address system.[6] The apparent threat of exhaustion was the motivation for remedial technologies, such as the introduction of classful networks, the creation of Classless Inter-Domain Routing (CIDR) methods, and network address translation (NAT), and finally for the redesign of the Internet Protocol, based on a larger address format (IPv6).Several market forces have driven the acceleration of IPv4 address exhaustion:
- Rapidly growing number of Internet users
- Always-on devices — ADSL modems, cable modems
- Mobile devices — laptop computers, PDAs, mobile phones
- Network address translation (NAT) is a technology that masquerades an entire, private network with a single public IP address, permitting the use of private addresses within the private network.
- Use of private networks
- Dynamic Host Configuration Protocol (DHCP)
- Name-based virtual hosting of web sites
- Tighter control by regional Internet registries over the allocation of addresses to local Internet registries
- Network renumbering to reclaim large blocks of address space allocated in the early days of the Internet
The accepted and standardized solution is the migration to Internet Protocol Version 6. The address size was increased in IPv6 to 128 bits, providing a vastly increased address space that also allows improved route aggregation across the Internet and offers large subnetwork allocations of a minimum of 264 host addresses to end-users. Migration to IPv6 is in progress but completion is expected to take considerable time.
[edit] Packet structure
An IP packet consists of a header section and a data section.[edit] Header
The IPv4 packet header consists of 14 fields, of which 13 are required. The 14th field is optional (red background in table) and aptly named: options. The fields in the header are packed with the most significant byte first (big endian), and for the diagram and discussion, the most significant bits are considered to come first (MSB 0 bit numbering). The most significant bit is numbered 0, so the version field is actually found in the four most significant bits of the first byte, for example.| bit offset | 0–3 | 4–7 | 8–13 | 14-15 | 16–18 | 19–31 | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | Version | Header Length | Differentiated Services Code Point | Explicit Congestion Notification | Total Length | |||||||||||||||||||||||||||
| 32 | Identification | Flags | Fragment Offset | |||||||||||||||||||||||||||||
| 64 | Time to Live | Protocol | Header checksum | |||||||||||||||||||||||||||||
| 96 | Source IP Address | |||||||||||||||||||||||||||||||
| 128 | Destination IP Address | |||||||||||||||||||||||||||||||
| 160 | Options ( if Header Length > 5 ) | |||||||||||||||||||||||||||||||
| 160 or 192+ |
Data | |||||||||||||||||||||||||||||||
7 OSI Layer
Model Jaringan 7 OSI Layer
Pengantar Model Open Systems Interconnection(OSI)Model Open Systems Interconnection (OSI) diciptakan oleh International Organization for Standardization (ISO) yang menyediakan kerangka logika terstruktur bagaimana proses komunikasi data berinteraksi melalui jaringan. Standard ini dikembangkan untuk industri komputer agar komputer dapat berkomunikasi pada jaringan yang berbeda secara efisien.
Model Layer OSI
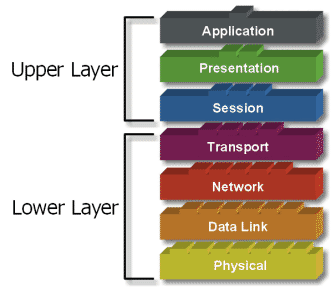
Terdapat 7 layer pada model OSI. Setiap layer bertanggungjawwab secara khusus pada proses komunikasi data. Misal, satu layer bertanggungjawab untuk membentuk koneksi antar perangkat, sementara layer lainnya bertanggungjawab untuk mengoreksi terjadinya “error” selama proses transfer data berlangsung.
Model Layer OSI dibagi dalam dua group: “upper layer” dan “lower layer”. “Upper layer” fokus pada applikasi pengguna dan bagaimana file direpresentasikan di komputer. Untuk Network Engineer, bagian utama yang menjadi perhatiannya adalah pada “lower layer”. Lower layer adalah intisari komunikasi data melalui jaringan aktual.
“Open” dalam OSI
 “Openâ€
dalam OSI adalah untuk menyatakan model jaringan yang melakukan
interkoneksi tanpa memandang perangkat keras/ “hardware” yang digunakan,
sepanjang software komunikasi sesuai dengan standard. Hal ini secara
tidak langsung menimbulkan “modularity” (dapat dibongkar pasang).
“Openâ€
dalam OSI adalah untuk menyatakan model jaringan yang melakukan
interkoneksi tanpa memandang perangkat keras/ “hardware” yang digunakan,
sepanjang software komunikasi sesuai dengan standard. Hal ini secara
tidak langsung menimbulkan “modularity” (dapat dibongkar pasang).Modularity
“Modularity” mengacu pada pertukaran protokol di level tertentu tanpa mempengaruhi atau merusak hubungan atau fungsi dari level lainnya.
Dalam sebuah layer, protokol saling dipertukarkan, dan memungkinkan komunikasi terus berlangsung. Pertukaran ini berlangsung didasarkan pada perangkat keras “hardware” dari vendor yang berbeda dan bermacam-macam alasan atau keinginan yang berbeda.
|
Modularity
|
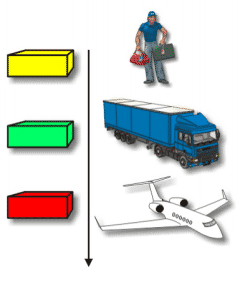 |
| Seperti contoh Jasa Antar/Kurir. “Modularity” pada level transportasi menyatakan bahwa tidak penting, bagaimana cara paket sampai ke pesawat. |
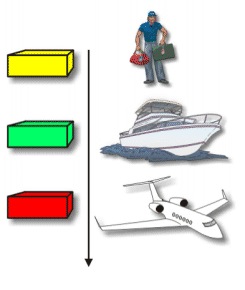 |
| Paket untuk sampai di pesawat, dapat dikirim melalui truk atau kapal. Masing-masing cara tersebut, pengirim tetap mengirimkan dan berharap paket tersebut sampai di Toronto. Pesawat terbang membawa paket ke Toronto tanpa memperhatikan bagaimana paket tersebut sampai di pesawat itu. |
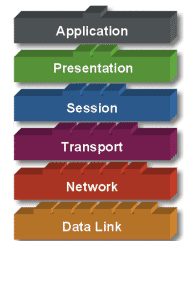
Model OSI terdiri dari 7 layer :
- Application
- Presentation
- Session
- Transport
- Network
- Data Link
- Physical
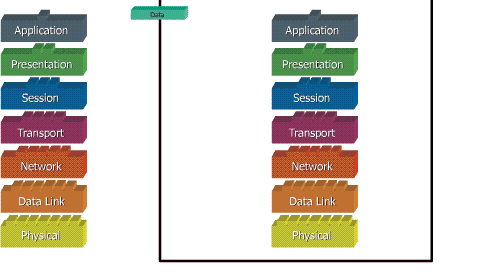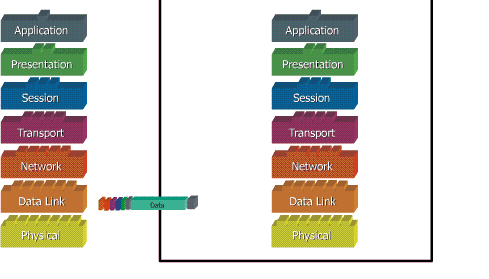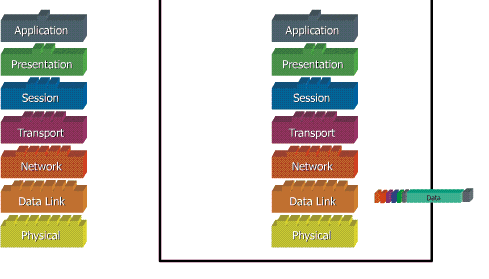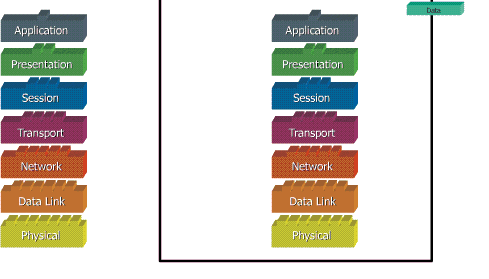
Ketika data ditransfer melalui jaringan, sebelumnya data tersebut harus melewati ke-tujuh layer dari satu terminal, mulai dari layer aplikasi sampai physical layer, kemudian di sisi penerima, data tersebut melewati layer physical sampai aplikasi. Pada saat data melewati satu layer dari sisi pengirim, maka akan ditambahkan satu “header” sedangkan pada sisi penerima “header” dicopot sesuai dengan layernya.
Model OSI
Tujuan utama penggunaan model OSI adalah untuk membantu desainer jaringan memahami fungsi dari tiap-tiap layer yang berhubungan dengan aliran komunikasi data. Termasuk jenis-jenis protoklol jaringan dan metode transmisi.
Model dibagi menjadi 7 layer, dengan karakteristik dan fungsinya masing-masing. Tiap layer harus dapat berkomunikasi dengan layer di atasnya maupun dibawahnya secara langsung melalui serentetan protokol dan standard.
|
Model OSI
|
Keterangan
|
 |
Application Layer: Menyediakan
jasa untuk aplikasi pengguna. Layer ini bertanggungjawab atas pertukaran
informasi antara program komputer, seperti program e-mail, dan service
lain yang jalan di jaringan, seperti server printer atau aplikasi
komputer lainnya.
|
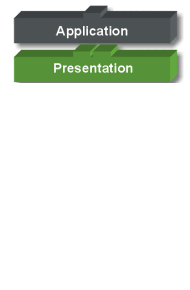 |
Presentation Layer: Bertanggung
jawab bagaimana data dikonversi dan diformat untuk transfer data. Contoh
konversi format text ASCII untuk dokumen, .gif dan JPG untuk gambar.
Layer ini membentuk kode konversi, translasi data, enkripsi dan
konversi.
|
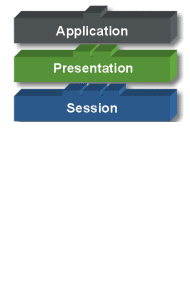 |
Session Layer: Menentukan
bagaimana dua terminal menjaga, memelihara dan mengatur koneksi,-
bagaimana mereka saling berhubungan satu sama lain. Koneksi di layer ini
disebut “session”.
|
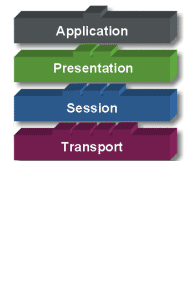 |
Transport Layer: Bertanggung jawab
membagi data menjadi segmen, menjaga koneksi logika “end-to-end” antar
terminal, dan menyediakan penanganan error (error handling).
|
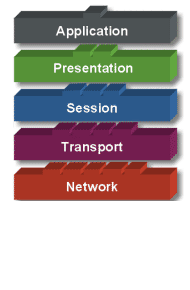 |
Network Layer: Bertanggung jawab
menentukan alamat jaringan, menentukan rute yang harus diambil selama
perjalanan, dan menjaga antrian trafik di jaringan. Data pada layer ini
berbentuk paket.
|
 |
Data Link Layer: Menyediakan link
untuk data, memaketkannya menjadi frame yang berhubungan dengan
“hardware” kemudian diangkut melalui media. komunikasinya dengan kartu
jaringan, mengatur komunikasi layer physical antara sistem koneksi dan
penanganan error.
|
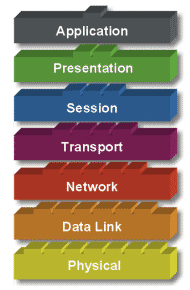 |
Physical Layer:
Bertanggung jawab atas proses data menjadi bit dan mentransfernya
melalui media, seperti kabel, dan menjaga koneksi fisik antar sistem.
|
Kamis, 16 Februari 2012
Contoh Naskah Sandiwara Radio
Kisah Sial Di Malam Minggu
(Karya kelompok Warrior FM D3 Penyiaran 2006 Fisip UI – dengan sejumlah editing)
NARATOR: Suasana malam minggu di taman lawang. Tampak beberapa waria Sedang berdiri di pinggir jalan. Menunggu kedatangan pria hidung belang.
SFX: SUASANA MALAM, BUNYI JANGKRIK (FADE UNDER)
MERRY: Aduh Betty…! malem ini sepi banget ya??? Nggak ada yang cucok gimana gitu…
BETTY: Iya nih Merry, tumben. Perasaan eike kemaren bisa sampe lima brondong deh. Ngantri di sindang. Uh, sebel…
SFX: SUARA MOBIL DATANG (FADE UNDER)
BETTY: Eh Merry, ada pasien tuh
MERRY: Wow, boleh tuh.. eh Betty, kita cegat yuk!
SFX: SUARA REM MOBIL (FADE OUT)
MUSIK: ROMANTIS (FADE UNDER)
MERRY: Hai cowok… godain kita dong, kita-kita lagi pada kosong nih..
PRIA: Iiih, ngapain amat? Mending gue ngejablay sekalian. Ogah banget sama lo, cuma setengah-setengah!
BETTY: Eh, enak aja! Siapa bilang kita setengah-setengah?? Kita 60-40 tau!
PRIA: Mau setengah-setengah kek, mau 60-40 kek! Gue lebih demen sama yang 100% asli tulen! Ogah ah, najis lo!
MUSIC: ROMANTIS (FADE OUT)
SFX: SUARA MOBIL MELAJU (FADE OUT)
MERRY: (DENGAN SUARA PRIA – MARAH) Woi! Jangan kabur lo!
BETTY: Ya ampyun Merry, jangan sikap dong, kita kan lagi cari duit. Ntar kalo pada kabur gimana?
MERRY: Sorry bo, eike lupa! Abisnya eike kesel sih, emosi jiwa! Jutek banget tu lekong, kasar!
SFX: SUARA SIRINE DARI KEJAUHAN
BETTY: Tunggu tunggu Merry, lo denger suara itu nggak?
MERRY: Suara apaan sih, Betty?
SFX: SUARA SIRINE SEMAKIN MENDEKAT (FADE IN – OUT)
BETTY: Duh, Merry.. kuping lo korslet ya? Itu suara sirine tau!
MERRY: Masa sih??
SFX: SUARA REM MOBIL, PINTU DIBUKA
BETTY & MERRY: (DENGAN SUARA COWOK – BERTERIAK) Waaaa…!!! Tramtiiiiiib……!!! Laaaaarriiiiiii……!!!!
PETUGAS TRAMTIB: (BERTERIAK) Hei kau! Jangan lari kau!!!
MERRY: Ya ampyun bapak trantib, jangan gila dong.. orang ditangkep masa eike nggak lari sih??
SFX: SUARA KONYOL
NARATOR: Itu lah kisah sial Merry dan Betty di malam minggu. Simak kelanjutan ceritanya di hari dan waktu yang sama. Yang pasti hanya di 102,5 Warrior FM.
Langganan:
Komentar (Atom)
1.Database adalah kumpulan informasi yang disimpan di dalam komputer secara sistematik sehingga dapat diperiksa menggunakan suatu program komputer untuk memperoleh informasi dari basis data tersebut.
2.Database Relational adalah sebuah database yang terdiri dari koleksi dari tabel-tabel, yang masing-masing diberikan nama yang unik. Sebuah baris dalam tabel merepresentasikan sebuah keterhubungan/relationship dari beberapa nilai yang ada.
3.DBMS (DataBase Management System) adalah sistem yang secara khusus dibuat untuk memudahkan pemakai dalam mengelola basis data. Sistem ini dibuat untuk mengatasi kelemahan sistem pemrosesan yang berbasis berkas.
4.Program aplikasi adalah software program yang memiliki aktivitas pemrosesan perintah yang diperlukan untuk melaksanakan permintaan pengguna dengan tujuan tertentu
5.Sistem data base merupakan perpaduan antarabasis data dan system manajemen basis data (SMBD).
6.Data adalah himpunan simbol atau fakta mentah yang tidak mempunyai arti dan nilai apapun secara tersendiri.
7.Informasi adalah data yang telah diproses menjadi bentuk yang memiliki arti bagi penerima dan dapat berupa fakta, suatu nilai yang bermanfaat.
8.Tabel adalah kumpulan dari beberapa record dan fields. jadi yang dimaksud dengan fields adalah atribut yang dimiliki oleh suatu tabel.
9.Formulir adalah secarik kertas yang memiliki ruang untuk diisi dengan data penting tertentu.
10.Record adalah kumpulan elemen-elemen data yang digabungkan menjadi satu kesatuan, masing-nasing elemen data tersebut dikenal dengan sebutan field.
11.Query adalah merupakan bahasa untuk melakukan manipulasi terhadap database, yang telah distandarkan dan lebih dikenal dengan nama Structured Query Language (SQL).
12.Field adalah sebuah unit data yang berisi satu atau lebih karakter (byte).
13.Report adalah file yang berisi data yang dibuat untuk laporan atau keperluan user. File tersebut dapat dicetak pada kertas printer atau hanya ditampilkan dilayar.
14.Primary Key adalah atribut (field) yang dipilih untuk menentukan struktur storage pada organisasi file multi key, adapun key lainnya disebut dengan secondary key.
2.Database Relational adalah sebuah database yang terdiri dari koleksi dari tabel-tabel, yang masing-masing diberikan nama yang unik. Sebuah baris dalam tabel merepresentasikan sebuah keterhubungan/relationship dari beberapa nilai yang ada.
3.DBMS (DataBase Management System) adalah sistem yang secara khusus dibuat untuk memudahkan pemakai dalam mengelola basis data. Sistem ini dibuat untuk mengatasi kelemahan sistem pemrosesan yang berbasis berkas.
4.Program aplikasi adalah software program yang memiliki aktivitas pemrosesan perintah yang diperlukan untuk melaksanakan permintaan pengguna dengan tujuan tertentu
5.Sistem data base merupakan perpaduan antarabasis data dan system manajemen basis data (SMBD).
6.Data adalah himpunan simbol atau fakta mentah yang tidak mempunyai arti dan nilai apapun secara tersendiri.
7.Informasi adalah data yang telah diproses menjadi bentuk yang memiliki arti bagi penerima dan dapat berupa fakta, suatu nilai yang bermanfaat.
8.Tabel adalah kumpulan dari beberapa record dan fields. jadi yang dimaksud dengan fields adalah atribut yang dimiliki oleh suatu tabel.
9.Formulir adalah secarik kertas yang memiliki ruang untuk diisi dengan data penting tertentu.
10.Record adalah kumpulan elemen-elemen data yang digabungkan menjadi satu kesatuan, masing-nasing elemen data tersebut dikenal dengan sebutan field.
11.Query adalah merupakan bahasa untuk melakukan manipulasi terhadap database, yang telah distandarkan dan lebih dikenal dengan nama Structured Query Language (SQL).
12.Field adalah sebuah unit data yang berisi satu atau lebih karakter (byte).
13.Report adalah file yang berisi data yang dibuat untuk laporan atau keperluan user. File tersebut dapat dicetak pada kertas printer atau hanya ditampilkan dilayar.
14.Primary Key adalah atribut (field) yang dipilih untuk menentukan struktur storage pada organisasi file multi key, adapun key lainnya disebut dengan secondary key.
Banyak lulusan TI Indonesia yang kemarin
di rendahkan (dilecehkan) ketika melamar pekerjaan hanya karena tidak
menguasai dasar-dasar jenis per-kabelan. Berita tentang TI Indonesia yang mengecewakan ini sampai sempat membuat beberapa orang panas. Panasnya kenapa? ada yang memang tidak tau menau tapi hanya ikutan “asal ngomong”
ada yang begini-begitu tapi ternyata ada saja alasannya, kenapa kita
harus teriak omong kosong kalau tidak mau menerima kritik dan belajar.
Memang umum-nya lulusan TI jaman
sekarang ini saya rasa belum siap untuk bekerja di bidangnya. Karena
teknologi yang selalu berkembang sehingga terkadang beberapa lulusan TI
ini merasa “mampu” padahal sebenarnya pemahaman dasar-nya dia tidak
punya. Kurikulum yang di kembangkan kampus juga terkadang tidak relevan
dengan realita yang ada di lapangan. Sehingga rasanya terkesan lebih
pandai orang yang terbiasa menggunakan dan ber-eksperimen di bandingkan
dengan orang yang hanya membahas teori.
Dalam artikel ini akan saya berikan
sedikit penjelasan tentang jenis-jenis per-kabelan, mudah-mudahan bisa
membuka wawasan dan membantu beberapa orang yang memang benar-benar
BUTA.
Peralatan dan media yang di butuhkan:

Urutan Ujung A
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Menghubungkan PC dengan HUB/Switch.

Urutan Ujung A
- Putih Orange
- Orange
- Putih Hijau
- Biru
- Putih Biru
- Hijau
- Putih Coklat
- Coklat
- Putih Hijau
- Hijau
- Putih Orange
- Putih Coklat
- Coklat
- Orange
- Biru
- Putih Biru
- Menghubungkan PC ke PC langsung tanpa HUB/Switch.
- Menghubungkan HUB/Swicth dengan HUB/Switch.
Kita akan coba membuat kabel straight,
pertama kupas-lah pelindung luar kabel UTP lalu atur agar lurus
kabel-kabel didalamnya. Urutkan posisinya berdasarkan diagram diatas.
Potong ujung kabel dengan gunting agar rata. Masukkan kedalam konektor
RJ-45 lalu di crimping dengan tang crimping. Ikuti caranya untuk ujung
kedua sama dengan langkah pertama. Masukkan ujung kedua kabel kedalam
LAN-tester lalu periksa, jika semua lampu 1-8 terhubung maka kabel ini
sudah siap kita pakai.
Untuk kabel cross juga sama seperti
langkah diatas, hanya bedanya harap perhatikan salah satu ujung yang
berbeda. Adapun standard per-kabelan ini yang dijaminkan adalah kurang
lebh 100 meter, diatas 100 meter kemungkinan akan mengalami loss.
Jika ada yang bertanya bagaimana
membedakan kabel straight dan kabel cross? Sebenarnya mudah saja,
perhatikan ujung dari kedua kabel tersebut lihat diagram-nya bila yang
pertama adalah putih orange lalu kedua putih orange juga sudah pasti itu
kabel straight, sedangkan kabel cross salah satu ujungnya dimulai
dengan putih hijau.
Internet Protocol version 4 (IPv4) is the fourth revision in the development of the Internet Protocol (IP) and the first version of the protocol to be widely deployed. Together with IPv6, it is at the core of standards-based internetworking methods of the Internet. IPv4 is still by far the most widely deployed Internet Layer protocol (As of 2011, IPv6 deployment is still in its infancy).
IPv4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition (RFC 760, January 1980).
IPv4 is a connectionless protocol for use on packet-switched Link Layer networks (e.g., Ethernet). It operates on a best effort delivery model, in that it does not guarantee delivery, nor does it assure proper sequencing or avoidance of duplicate delivery. These aspects, including data integrity, are addressed by an upper layer transport protocol , such as the Transmission Control Protocol (TCP).
This limitation stimulated the development of IPv6 in the 1990s, which has been in commercial deployment since 2006.
The following table shows several representation formats:
To overcome this limit, the high order octet of the addresses was redefined to create a set of classes of networks, in a system which later became known as classful networking. The system defined five classes, Class A, B, C, D, and E. The Classes A, B, and C had different bit lengths for the new network identification. The rest of an address was used as previously to identify a host within a network, which meant that each network class had a different capacity to address hosts. Class D was allocated for multicast addressing and Class E was reserved for future applications.
Starting around 1985, methods were devised to allow IP networks to be subdivided. The concept of the variable-length subnet mask (VLSM) was introduced which allowed flexible subdivision into varying network sizes.[2][3]
Around 1993, this system of classes was officially replaced with Classless Inter-Domain Routing (CIDR), and the class-based scheme was dubbed classful, by contrast.
CIDR was designed to permit repartitioning of any address space so that smaller or larger blocks of addresses could be allocated to users. The hierarchical structure created by CIDR is managed by the Internet Assigned Numbers Authority (IANA) and the regional Internet registries (RIRs). Each RIR maintains a publicly-searchable WHOIS database that provides information about IP address assignments.
The following are the three ranges reserved for private networks (RFC 1918):
VPNs establish tunneling connections across the public network such that the endpoints of the tunnel function as routers for packets from the private network. In this routing function the host encapsulates packets in a protocol layer with packet headers acceptable in the public network so that they may be delivered to the opposing tunnel end point where the additional protocol layer is removed and the packet is delivered locally to its intended destination.
Optionally, encapsulated packets may be encrypted to secure the data while it travels over the public network.
When the address block was reserved, no standards existed for mechanisms of address autoconfiguration. Filling the void, Microsoft created an implementation called Automatic Private IP Addressing (APIPA). Due to Microsoft's market power, APIPA has been deployed on millions of machines and has, thus, become a de facto standard in the industry. Many years later, the IETF defined a formal standard for this functionality, RFC 3927, entitled Dynamic Configuration of IPv4 Link-Local Addresses.
Classful addressing prescribed only three possible subnet masks: Class A, 255.0.0.0 or /8; Class B, 255.255.0.0 or /16; and Class C, 255.255.255.0 or /24. For example, in the subnet 192.168.5.0/255.255.255.0 (192.168.5.0/24) the identifier 192.168.5.0 commonly is used to refer to the entire subnet. To avoid ambiguity in representation, the address ending in the octet 0 is reserved.
A broadcast address is an address that allows information to be sent to all interfaces in a given subnet, rather than a specific machine. Generally, the broadcast address is found by obtaining the bit complement of the subnet mask and performing a bitwise OR operation with the network identifier. In other words, the broadcast address is the last address in the address range of the subnet. For example, the broadcast address for the network 192.168.5.0 is 192.168.5.255. For networks of size /24 or larger, the broadcast address always ends in 255.
However, this does not mean that every address ending in 0 or 255 cannot be used as a host address. For example, in the case of a /16 subnet 192.168.0.0/255.255.0.0, equivalent to the address range 192.168.0.0–192.168.255.255, the broadcast address is 192.168.255.255. However, one may assign 192.168.1.255, 192.168.2.255, etc. 192.168.0.0 is the network identifier which should not be assigned to an interface,[4] but 192.168.1.0, 192.168.2.0, etc. may be assigned.
In the past, conflict between network addresses and broadcast addresses arose because some software used non-standard broadcast addresses with zeros instead of ones.[5]
In networks smaller than /24, broadcast addresses do not necessarily end with 255. For example, a CIDR subnet 203.0.113.16/28 has the broadcast address 203.0.113.31.
The translation between addresses and domain names is performed by the Domain Name System (DNS), a hierarchical, distributed naming system which allows for subdelegation of name spaces to other DNS servers. DNS is often described in analogy to the telephone system directory information systems in which subscriber names are translated to telephone numbers.
Several market forces have driven the acceleration of IPv4 address exhaustion:
The accepted and standardized solution is the migration to Internet Protocol Version 6. The address size was increased in IPv6 to 128 bits, providing a vastly increased address space that also allows improved route aggregation across the Internet and offers large subnetwork allocations of a minimum of 264 host addresses to end-users. Migration to IPv6 is in progress but completion is expected to take considerable time.
IPv4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition (RFC 760, January 1980).
IPv4 is a connectionless protocol for use on packet-switched Link Layer networks (e.g., Ethernet). It operates on a best effort delivery model, in that it does not guarantee delivery, nor does it assure proper sequencing or avoidance of duplicate delivery. These aspects, including data integrity, are addressed by an upper layer transport protocol , such as the Transmission Control Protocol (TCP).
| Internet protocol suite |
|---|
| Application layer |
| Transport layer |
| Internet layer |
| Link layer |
Contents[hide] |
[edit] Addressing
IPv4 uses 32-bit (four-byte) addresses, which limits the address space to 4294967296 (232) addresses. However, some address blocks are reserved for special purposes such as private networks (~18 million addresses) and multicast addresses (~270 million addresses). This reduces the number of addresses that may be allocated for routing on the public Internet. As addresses are assigned to end users, an IPv4 address shortage has been developing. Network addressing changes by classful network design, Classless Inter-Domain Routing, and network address translation (NAT) have contributed to delay significantly the inevitable exhaustion which occurred on February 3, 2011 when IANA allocated the last five blocks to the five regional Internet registries (RIRs).This limitation stimulated the development of IPv6 in the 1990s, which has been in commercial deployment since 2006.
[edit] Address representations
IPv4 addresses may be written in any notation expressing a 32-bit integer value, but for human convenience, they are most often written in dot-decimal notation, which consists of four octets of the address expressed individually in decimal and separated by periods.The following table shows several representation formats:
| Notation | Value | Conversion from dot-decimal |
|---|---|---|
| Dot-decimal notation | 192.0.2.235 | N/A |
| Dotted Hexadecimal[1] | 0xC0.0x00.0x02.0xEB | Each octet is individually converted to hexadecimal form |
| Dotted Octal[1] | 0300.0000.0002.0353 | Each octet is individually converted into octal |
| Hexadecimal | 0xC00002EB | Concatenation of the octets from the dotted hexadecimal |
| Decimal | 3221226219 | The 32-bit number expressed in decimal |
| Octal | 030000001353 | The 32-bit number expressed in octal |
[edit] Allocation
Originally, an IP address was divided into two parts, the network identifier represented in the most significant (highest order) octet of the address and the host identifier using the rest of the address. The latter was therefore also called the rest field. This enabled the creation of a maximum of 256 networks. This was quickly found to be inadequate.To overcome this limit, the high order octet of the addresses was redefined to create a set of classes of networks, in a system which later became known as classful networking. The system defined five classes, Class A, B, C, D, and E. The Classes A, B, and C had different bit lengths for the new network identification. The rest of an address was used as previously to identify a host within a network, which meant that each network class had a different capacity to address hosts. Class D was allocated for multicast addressing and Class E was reserved for future applications.
Starting around 1985, methods were devised to allow IP networks to be subdivided. The concept of the variable-length subnet mask (VLSM) was introduced which allowed flexible subdivision into varying network sizes.[2][3]
Around 1993, this system of classes was officially replaced with Classless Inter-Domain Routing (CIDR), and the class-based scheme was dubbed classful, by contrast.
CIDR was designed to permit repartitioning of any address space so that smaller or larger blocks of addresses could be allocated to users. The hierarchical structure created by CIDR is managed by the Internet Assigned Numbers Authority (IANA) and the regional Internet registries (RIRs). Each RIR maintains a publicly-searchable WHOIS database that provides information about IP address assignments.
[edit] Special-use addresses
Main article: Reserved IP addresses#Reserved IPv4 addresses
| CIDR address block | Description | Reference |
|---|---|---|
| 0.0.0.0/8 | Current network (only valid as source address) | RFC 1700 |
| 10.0.0.0/8 | Private network | RFC 1918 |
| 127.0.0.0/8 | Loopback | RFC 5735 |
| 169.254.0.0/16 | Link-Local | RFC 3927 |
| 172.16.0.0/12 | Private network | RFC 1918 |
| 192.0.0.0/24 | Reserved (IANA) | RFC 5735 |
| 192.0.2.0/24 | TEST-NET-1, Documentation and example code | RFC 5735 |
| 192.88.99.0/24 | IPv6 to IPv4 relay | RFC 3068 |
| 192.168.0.0/16 | Private network | RFC 1918 |
| 198.18.0.0/15 | Network benchmark tests | RFC 2544 |
| 198.51.100.0/24 | TEST-NET-2, Documentation and examples | RFC 5737 |
| 203.0.113.0/24 | TEST-NET-3, Documentation and examples | RFC 5737 |
| 224.0.0.0/4 | Multicasts (former Class D network) | RFC 3171 |
| 240.0.0.0/4 | Reserved (former Class E network) | RFC 1700 |
| 255.255.255.255 | Broadcast | RFC 919 |
[edit] Private networks
Of the approximately four billion addresses allowed in IPv4, three ranges of address are reserved for use in private networks. These ranges are not routable outside of private networks and private machines cannot directly communicate with public networks. They can, however, do so through network address translation.The following are the three ranges reserved for private networks (RFC 1918):
| Name | Address range | Number of addresses | Classful description | Largest CIDR block |
|---|---|---|---|---|
| 24-bit block | 10.0.0.0–10.255.255.255 | 16777216 | Single Class A | 10.0.0.0/8 |
| 20-bit block | 172.16.0.0–172.31.255.255 | 1048576 | Contiguous range of 16 Class B blocks | 172.16.0.0/12 |
| 16-bit block | 192.168.0.0–192.168.255.255 | 65536 | Contiguous range of 256 Class C blocks | 192.168.0.0/16 |
[edit] Virtual private networks
Packets with a private destination address are ignored by all public routers. Therefore, it is not possible to communicate directly between two private networks (e.g., two branch offices) via the public Internet. This requires the use of IP tunnels or a virtual private network (VPN).VPNs establish tunneling connections across the public network such that the endpoints of the tunnel function as routers for packets from the private network. In this routing function the host encapsulates packets in a protocol layer with packet headers acceptable in the public network so that they may be delivered to the opposing tunnel end point where the additional protocol layer is removed and the packet is delivered locally to its intended destination.
Optionally, encapsulated packets may be encrypted to secure the data while it travels over the public network.
[edit] Link-local addressing
Main article: Link-local address
RFC 5735
defines an address block, 169.254.0.0/16, for the special use in
link-local addressing. These addresses are only valid on the link, such
as a local network segment or point-to-point connection, that a host is
connected to. These addresses are not routable and like private
addresses cannot be the source or destination of packets traversing the
Internet. Link-local addresses are primarily used for address
autoconfiguration (Zeroconf) when a host cannot obtain an IP address from a DHCP server or other internal configuration methods.When the address block was reserved, no standards existed for mechanisms of address autoconfiguration. Filling the void, Microsoft created an implementation called Automatic Private IP Addressing (APIPA). Due to Microsoft's market power, APIPA has been deployed on millions of machines and has, thus, become a de facto standard in the industry. Many years later, the IETF defined a formal standard for this functionality, RFC 3927, entitled Dynamic Configuration of IPv4 Link-Local Addresses.
[edit] Localhost
Main article: localhost
The address range 127.0.0.0–127.255.255.255 (127.0.0.0/8 in CIDR notation) is reserved for localhost
communication. Addresses within this range should never appear outside a
host computer and packets sent to this address are returned as incoming
packets on the same virtual network device (known as loopback).[edit] Addresses ending in 0 or 255
Main article: IPv4 subnetting reference
Networks with subnet masks of at least 24 bits, i.e. Class C networks
in classful networking, and networks with CIDR prefixes /24 to /32
(255.255.255.0–255.255.255.255) may not have an address ending in 0 or
255.Classful addressing prescribed only three possible subnet masks: Class A, 255.0.0.0 or /8; Class B, 255.255.0.0 or /16; and Class C, 255.255.255.0 or /24. For example, in the subnet 192.168.5.0/255.255.255.0 (192.168.5.0/24) the identifier 192.168.5.0 commonly is used to refer to the entire subnet. To avoid ambiguity in representation, the address ending in the octet 0 is reserved.
A broadcast address is an address that allows information to be sent to all interfaces in a given subnet, rather than a specific machine. Generally, the broadcast address is found by obtaining the bit complement of the subnet mask and performing a bitwise OR operation with the network identifier. In other words, the broadcast address is the last address in the address range of the subnet. For example, the broadcast address for the network 192.168.5.0 is 192.168.5.255. For networks of size /24 or larger, the broadcast address always ends in 255.
However, this does not mean that every address ending in 0 or 255 cannot be used as a host address. For example, in the case of a /16 subnet 192.168.0.0/255.255.0.0, equivalent to the address range 192.168.0.0–192.168.255.255, the broadcast address is 192.168.255.255. However, one may assign 192.168.1.255, 192.168.2.255, etc. 192.168.0.0 is the network identifier which should not be assigned to an interface,[4] but 192.168.1.0, 192.168.2.0, etc. may be assigned.
In the past, conflict between network addresses and broadcast addresses arose because some software used non-standard broadcast addresses with zeros instead of ones.[5]
In networks smaller than /24, broadcast addresses do not necessarily end with 255. For example, a CIDR subnet 203.0.113.16/28 has the broadcast address 203.0.113.31.
[edit] Address resolution
Main article: Domain Name System
Hosts on the Internet
are usually known by names, e.g., www.example.com, not primarily by
their IP address, which is used for routing and network interface
identification. The use of domain names requires translating, called resolving, them to addresses and vice versa. This is analogous to looking up a phone number in a phone book using the recipient's name.The translation between addresses and domain names is performed by the Domain Name System (DNS), a hierarchical, distributed naming system which allows for subdelegation of name spaces to other DNS servers. DNS is often described in analogy to the telephone system directory information systems in which subscriber names are translated to telephone numbers.
[edit] Address space exhaustion
Main article: IPv4 address exhaustion
Since the 1980s it was apparent that the pool of available IPv4
addresses was depleted at a rate that was not initially anticipated in
the original design of the network address system.[6] The apparent threat of exhaustion was the motivation for remedial technologies, such as the introduction of classful networks, the creation of Classless Inter-Domain Routing (CIDR) methods, and network address translation (NAT), and finally for the redesign of the Internet Protocol, based on a larger address format (IPv6).Several market forces have driven the acceleration of IPv4 address exhaustion:
- Rapidly growing number of Internet users
- Always-on devices — ADSL modems, cable modems
- Mobile devices — laptop computers, PDAs, mobile phones
- Network address translation (NAT) is a technology that masquerades an entire, private network with a single public IP address, permitting the use of private addresses within the private network.
- Use of private networks
- Dynamic Host Configuration Protocol (DHCP)
- Name-based virtual hosting of web sites
- Tighter control by regional Internet registries over the allocation of addresses to local Internet registries
- Network renumbering to reclaim large blocks of address space allocated in the early days of the Internet
The accepted and standardized solution is the migration to Internet Protocol Version 6. The address size was increased in IPv6 to 128 bits, providing a vastly increased address space that also allows improved route aggregation across the Internet and offers large subnetwork allocations of a minimum of 264 host addresses to end-users. Migration to IPv6 is in progress but completion is expected to take considerable time.
[edit] Packet structure
An IP packet consists of a header section and a data section.[edit] Header
The IPv4 packet header consists of 14 fields, of which 13 are required. The 14th field is optional (red background in table) and aptly named: options. The fields in the header are packed with the most significant byte first (big endian), and for the diagram and discussion, the most significant bits are considered to come first (MSB 0 bit numbering). The most significant bit is numbered 0, so the version field is actually found in the four most significant bits of the first byte, for example.| bit offset | 0–3 | 4–7 | 8–13 | 14-15 | 16–18 | 19–31 | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | Version | Header Length | Differentiated Services Code Point | Explicit Congestion Notification | Total Length | |||||||||||||||||||||||||||
| 32 | Identification | Flags | Fragment Offset | |||||||||||||||||||||||||||||
| 64 | Time to Live | Protocol | Header checksum | |||||||||||||||||||||||||||||
| 96 | Source IP Address | |||||||||||||||||||||||||||||||
| 128 | Destination IP Address | |||||||||||||||||||||||||||||||
| 160 | Options ( if Header Length > 5 ) | |||||||||||||||||||||||||||||||
| 160 or 192+ |
Data | |||||||||||||||||||||||||||||||
Model Jaringan 7 OSI Layer
Pengantar Model Open Systems Interconnection(OSI)Model Open Systems Interconnection (OSI) diciptakan oleh International Organization for Standardization (ISO) yang menyediakan kerangka logika terstruktur bagaimana proses komunikasi data berinteraksi melalui jaringan. Standard ini dikembangkan untuk industri komputer agar komputer dapat berkomunikasi pada jaringan yang berbeda secara efisien.
Model Layer OSI

Terdapat 7 layer pada model OSI. Setiap layer bertanggungjawwab secara khusus pada proses komunikasi data. Misal, satu layer bertanggungjawab untuk membentuk koneksi antar perangkat, sementara layer lainnya bertanggungjawab untuk mengoreksi terjadinya “error” selama proses transfer data berlangsung.
Model Layer OSI dibagi dalam dua group: “upper layer” dan “lower layer”. “Upper layer” fokus pada applikasi pengguna dan bagaimana file direpresentasikan di komputer. Untuk Network Engineer, bagian utama yang menjadi perhatiannya adalah pada “lower layer”. Lower layer adalah intisari komunikasi data melalui jaringan aktual.
“Open” dalam OSI
 “Openâ€
dalam OSI adalah untuk menyatakan model jaringan yang melakukan
interkoneksi tanpa memandang perangkat keras/ “hardware” yang digunakan,
sepanjang software komunikasi sesuai dengan standard. Hal ini secara
tidak langsung menimbulkan “modularity” (dapat dibongkar pasang).
“Openâ€
dalam OSI adalah untuk menyatakan model jaringan yang melakukan
interkoneksi tanpa memandang perangkat keras/ “hardware” yang digunakan,
sepanjang software komunikasi sesuai dengan standard. Hal ini secara
tidak langsung menimbulkan “modularity” (dapat dibongkar pasang).Modularity
“Modularity” mengacu pada pertukaran protokol di level tertentu tanpa mempengaruhi atau merusak hubungan atau fungsi dari level lainnya.
Dalam sebuah layer, protokol saling dipertukarkan, dan memungkinkan komunikasi terus berlangsung. Pertukaran ini berlangsung didasarkan pada perangkat keras “hardware” dari vendor yang berbeda dan bermacam-macam alasan atau keinginan yang berbeda.
|
Modularity
|
 |
| Seperti contoh Jasa Antar/Kurir. “Modularity” pada level transportasi menyatakan bahwa tidak penting, bagaimana cara paket sampai ke pesawat. |
 |
| Paket untuk sampai di pesawat, dapat dikirim melalui truk atau kapal. Masing-masing cara tersebut, pengirim tetap mengirimkan dan berharap paket tersebut sampai di Toronto. Pesawat terbang membawa paket ke Toronto tanpa memperhatikan bagaimana paket tersebut sampai di pesawat itu. |
Model OSI terdiri dari 7 layer :
- Application
- Presentation
- Session
- Transport
- Network
- Data Link
- Physical

Ketika data ditransfer melalui jaringan, sebelumnya data tersebut harus melewati ke-tujuh layer dari satu terminal, mulai dari layer aplikasi sampai physical layer, kemudian di sisi penerima, data tersebut melewati layer physical sampai aplikasi. Pada saat data melewati satu layer dari sisi pengirim, maka akan ditambahkan satu “header” sedangkan pada sisi penerima “header” dicopot sesuai dengan layernya.
Model OSI
Tujuan utama penggunaan model OSI adalah untuk membantu desainer jaringan memahami fungsi dari tiap-tiap layer yang berhubungan dengan aliran komunikasi data. Termasuk jenis-jenis protoklol jaringan dan metode transmisi.
Model dibagi menjadi 7 layer, dengan karakteristik dan fungsinya masing-masing. Tiap layer harus dapat berkomunikasi dengan layer di atasnya maupun dibawahnya secara langsung melalui serentetan protokol dan standard.
|
Model OSI
|
Keterangan
|
 |
Application Layer: Menyediakan
jasa untuk aplikasi pengguna. Layer ini bertanggungjawab atas pertukaran
informasi antara program komputer, seperti program e-mail, dan service
lain yang jalan di jaringan, seperti server printer atau aplikasi
komputer lainnya.
|
 |
Presentation Layer: Bertanggung
jawab bagaimana data dikonversi dan diformat untuk transfer data. Contoh
konversi format text ASCII untuk dokumen, .gif dan JPG untuk gambar.
Layer ini membentuk kode konversi, translasi data, enkripsi dan
konversi.
|
 |
Session Layer: Menentukan
bagaimana dua terminal menjaga, memelihara dan mengatur koneksi,-
bagaimana mereka saling berhubungan satu sama lain. Koneksi di layer ini
disebut “session”.
|
 |
Transport Layer: Bertanggung jawab
membagi data menjadi segmen, menjaga koneksi logika “end-to-end” antar
terminal, dan menyediakan penanganan error (error handling).
|
 |
Network Layer: Bertanggung jawab
menentukan alamat jaringan, menentukan rute yang harus diambil selama
perjalanan, dan menjaga antrian trafik di jaringan. Data pada layer ini
berbentuk paket.
|
 |
Data Link Layer: Menyediakan link
untuk data, memaketkannya menjadi frame yang berhubungan dengan
“hardware” kemudian diangkut melalui media. komunikasinya dengan kartu
jaringan, mengatur komunikasi layer physical antara sistem koneksi dan
penanganan error.
|
 |
Physical Layer:
Bertanggung jawab atas proses data menjadi bit dan mentransfernya
melalui media, seperti kabel, dan menjaga koneksi fisik antar sistem.
|
Kisah Sial Di Malam Minggu
(Karya kelompok Warrior FM D3 Penyiaran 2006 Fisip UI – dengan sejumlah editing)
NARATOR: Suasana malam minggu di taman lawang. Tampak beberapa waria Sedang berdiri di pinggir jalan. Menunggu kedatangan pria hidung belang.
SFX: SUASANA MALAM, BUNYI JANGKRIK (FADE UNDER)
MERRY: Aduh Betty…! malem ini sepi banget ya??? Nggak ada yang cucok gimana gitu…
BETTY: Iya nih Merry, tumben. Perasaan eike kemaren bisa sampe lima brondong deh. Ngantri di sindang. Uh, sebel…
SFX: SUARA MOBIL DATANG (FADE UNDER)
BETTY: Eh Merry, ada pasien tuh
MERRY: Wow, boleh tuh.. eh Betty, kita cegat yuk!
SFX: SUARA REM MOBIL (FADE OUT)
MUSIK: ROMANTIS (FADE UNDER)
MERRY: Hai cowok… godain kita dong, kita-kita lagi pada kosong nih..
PRIA: Iiih, ngapain amat? Mending gue ngejablay sekalian. Ogah banget sama lo, cuma setengah-setengah!
BETTY: Eh, enak aja! Siapa bilang kita setengah-setengah?? Kita 60-40 tau!
PRIA: Mau setengah-setengah kek, mau 60-40 kek! Gue lebih demen sama yang 100% asli tulen! Ogah ah, najis lo!
MUSIC: ROMANTIS (FADE OUT)
SFX: SUARA MOBIL MELAJU (FADE OUT)
MERRY: (DENGAN SUARA PRIA – MARAH) Woi! Jangan kabur lo!
BETTY: Ya ampyun Merry, jangan sikap dong, kita kan lagi cari duit. Ntar kalo pada kabur gimana?
MERRY: Sorry bo, eike lupa! Abisnya eike kesel sih, emosi jiwa! Jutek banget tu lekong, kasar!
SFX: SUARA SIRINE DARI KEJAUHAN
BETTY: Tunggu tunggu Merry, lo denger suara itu nggak?
MERRY: Suara apaan sih, Betty?
SFX: SUARA SIRINE SEMAKIN MENDEKAT (FADE IN – OUT)
BETTY: Duh, Merry.. kuping lo korslet ya? Itu suara sirine tau!
MERRY: Masa sih??
SFX: SUARA REM MOBIL, PINTU DIBUKA
BETTY & MERRY: (DENGAN SUARA COWOK – BERTERIAK) Waaaa…!!! Tramtiiiiiib……!!! Laaaaarriiiiiii……!!!!
PETUGAS TRAMTIB: (BERTERIAK) Hei kau! Jangan lari kau!!!
MERRY: Ya ampyun bapak trantib, jangan gila dong.. orang ditangkep masa eike nggak lari sih??
SFX: SUARA KONYOL
NARATOR: Itu lah kisah sial Merry dan Betty di malam minggu. Simak kelanjutan ceritanya di hari dan waktu yang sama. Yang pasti hanya di 102,5 Warrior FM.
Langganan:
Komentar (Atom)
















